TL;DR:
Need the IPA file for an iOS app? Here’s the straight-up advice:
Ask your mobile developer.
(Seriously… and also, kind of joking.)
When it comes to mobile security testing, most of the time clients or developers will hand you the IPA file, especially if you make it clear that it is part of your requirements. They might email it to you or share it through development-focused platforms like TestFlight, Visual Studio App Center, or Firebase App Distribution. It really depends on their workflow.
Sometimes, instead of waiting for someone to send the file, there are ways to get it yourself.
Table of contents
Open Table of contents
Method 1: Pull from the App Store
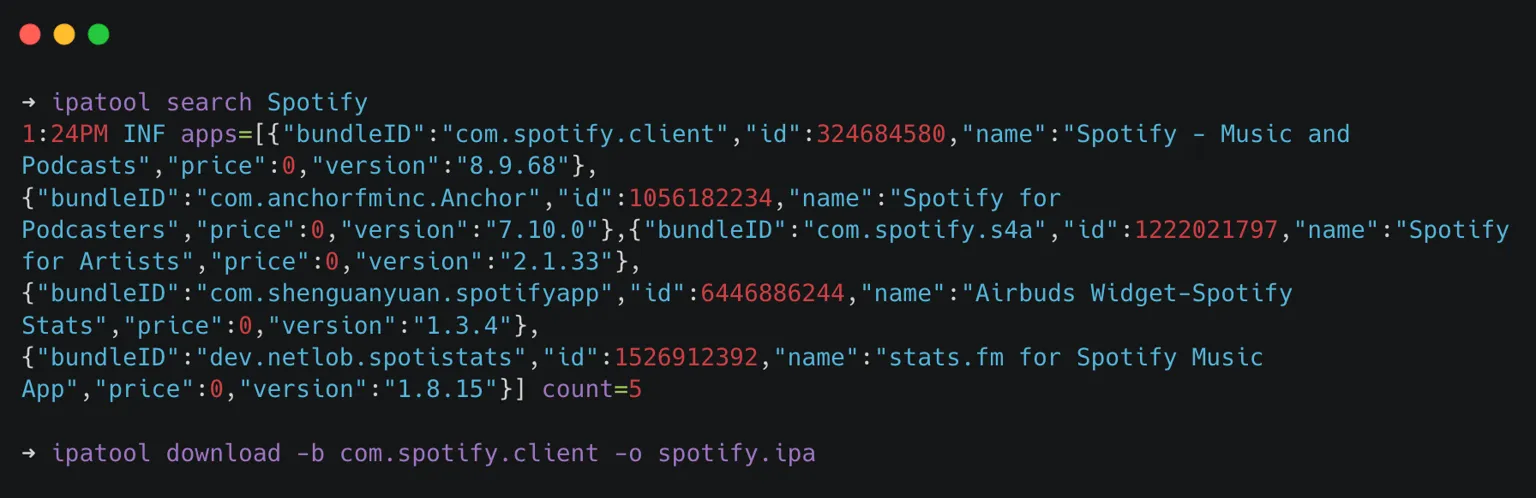
If you want to grab an IPA straight from the App Store, ipatool is your friend. It’s a command‑line tool that lets you download IPA files using your Apple ID, basically acting like a headless App Store client.
Installation (Mac Homebrew)
$ brew tap majd/repo
$ brew install ipatoolUsage
You need your Apple ID credentials for this tool to authenticate, just like a real App Store client.
$ ipatool auth
$ ipatool search Spotify
$ ipatool download -b com.spotify.client -o spotify.ipaMethod 2: Extract from Jailbroken Device
If you have a jailbroken device lying around, you can dump the decrypted IPA directly from the system. Since the app is already decrypted at runtime, this method gives you a clean package for analysis.
Opt A: Frida-ios-dump
This tool uses Frida under the hood to dump decrypted versions of apps from the device.
Note: This approach can be hit-or-miss depending on your iOS version, device, and Frida compatibility. I’ve run into plenty of issues with it, so if it gives you trouble, try the next option.
Opt B: Bagbak
A much more stable alternative in most cases.
npm install -g bagbakUse bagbak to decrypt the application and extract it from the iPhone. (Remember to set SSH username to root, password is alpine)
export SSH_USERNAME=root
✦ ➜ bagbak com.apple.iBooks
[info] pulling app bundle from device, please be patient
[info] downloaded 682 files and 511 folders
[info] app bundle downloaded
....
Saved to com.apple.iBooks-9.4.ipa